Using Action Control List
The Rich Text Editor Pro configuration can be dependent on user's application role using APEX core feature Authorization Schemes. The plug-in configuration dependent on user role can be implemented using:
- A dynamic action attribute authorization scheme
- A dynamic action attribute server-side condition
- The plug-in application attribute Initialization PL/SQL Code
- The plug-in page item attribute Initialization PL/SQL Code
- A page item standard attribute Initialization JavaScript Code supported by page PL/SQL process
Dynamic Actions
A dynamic action implementing the supporting dynamic action plug-in can be run depending on user's role in an application using dynamic action attribute Authorization Scheme, or can be run depending on evaluation od PL/SQL code using attribute Server-Side Condition.
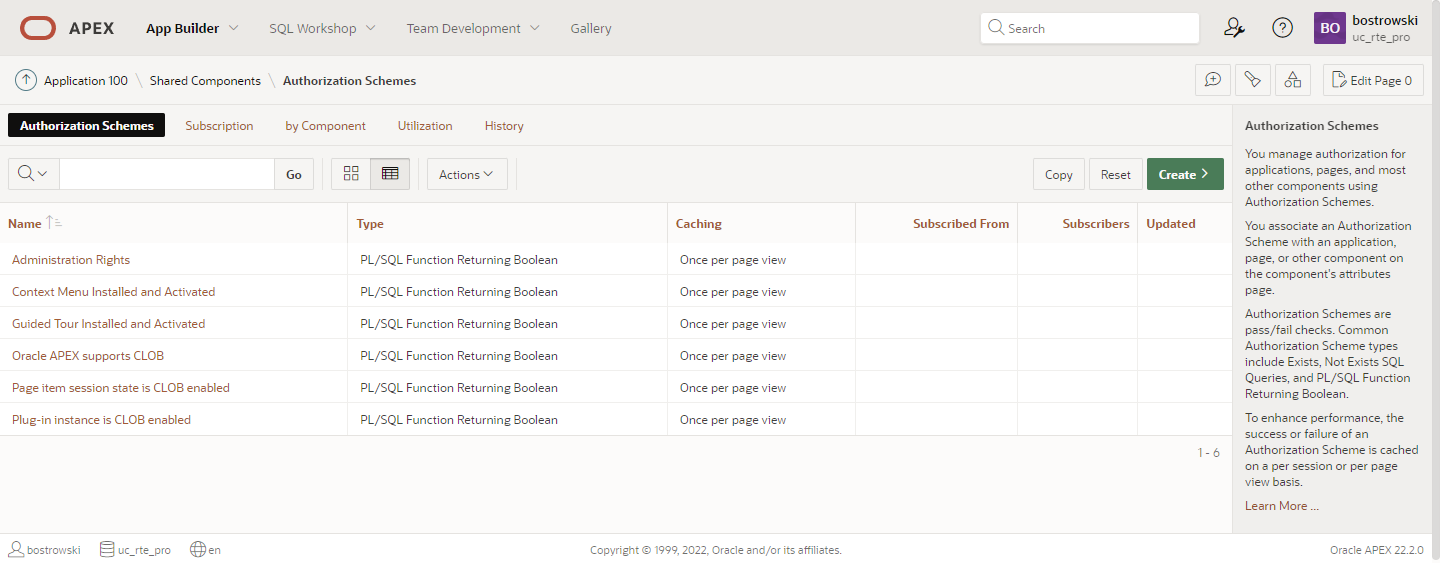
Authorization Scheme
A dynamic action security attribute allows selecting an application authorization scheme as the dynamic action execution condition. If authorization scheme result is negative, the dynamic action is not executed, thus the plug-in won't be configured, or a specified action won't be executed. On the other hand, when end-user is authorized, a dynamic action is executed.
- Validating
- Types
Oracle APEX authorization schemes can be validated
- once per session,
- once per page view,
- once per component,
- always (no caching).
Oracle APEX authorization schemes types are the following:
- Exists SQL Query
- Is In Role or Group
- Is Not In Role or Group
- Item in Expression 1 is NULL
- Item in Expression1 is NOT NULL
- NOT Exists SQL Query
- PL/SQL Function Returning Boolean
- Value of Item in Expression 1 Does NOT Equal Expression 2
- Value of Item in Expression 1 Equals Expression 2
- Value of Preference in Expression 1 Does NOT Equal Expression 2
- Value of Preference in Expression 1 Equals Expression 2
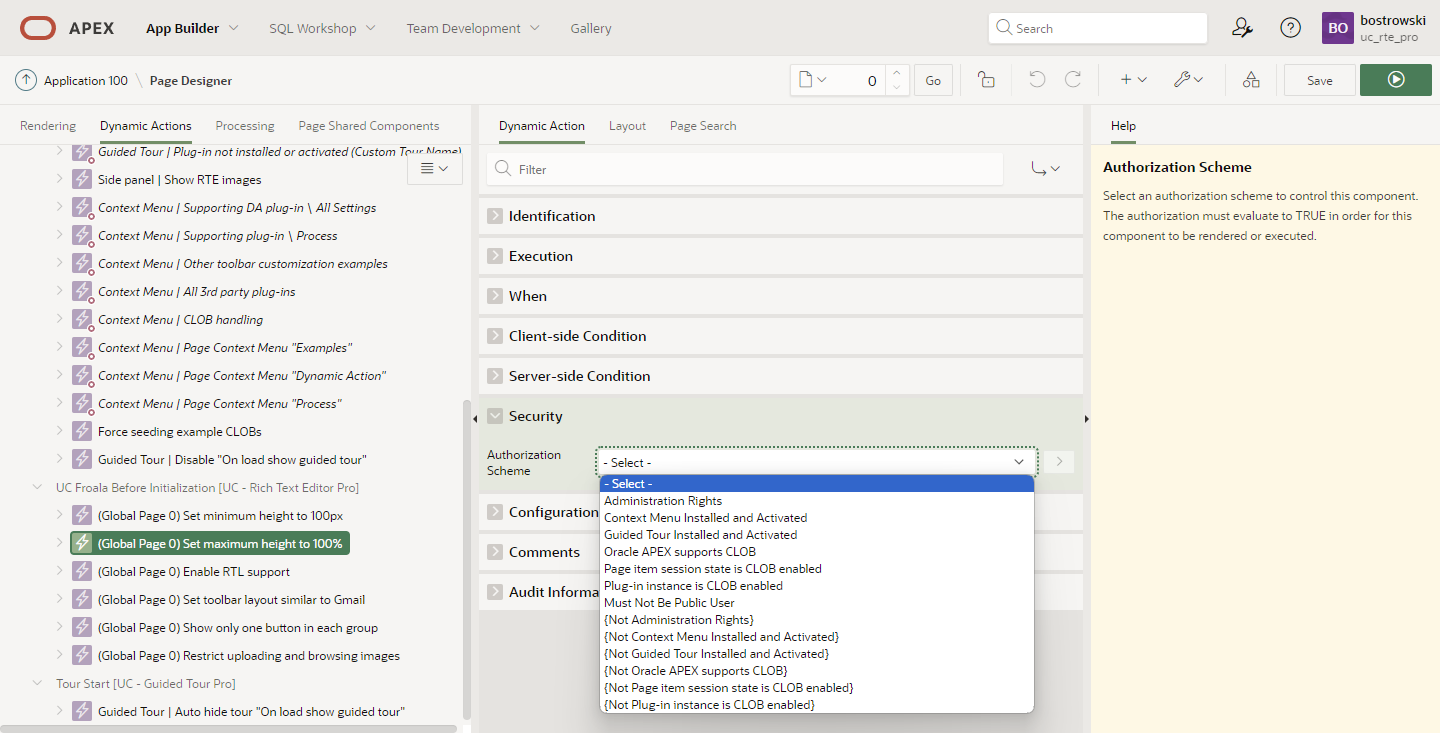
Applying authorization scheme is as easy as selecting existing component from list, see the screenshot from the plug-in sample application. The list presented in the security section is computed based on existing application authorization schemes in an application shared components.
- Dynamic Action Security
- Application Authorization Schemes
Server-side condition
The dynamic action attribute server-side condition determines whether a dynamic action will be executed. If the condition result is postive, a dynamic action is executed on specified triggering JavaScript event. Dynamic action server-side conditions can be used to create PL/SQL based plug-in configuration. It's very similar to authorization schemes, but the server-side conditions are always evaluated.
The complete list of server-side conditions can be found in Oracle APEX documentation. Server-side conditions PL/SQL Expression and PL/SQL Function Body allows implementing complex PL/SQL logic.
For example, server-side condition can be used to evaluate named authorization scheme, see screenshot below.
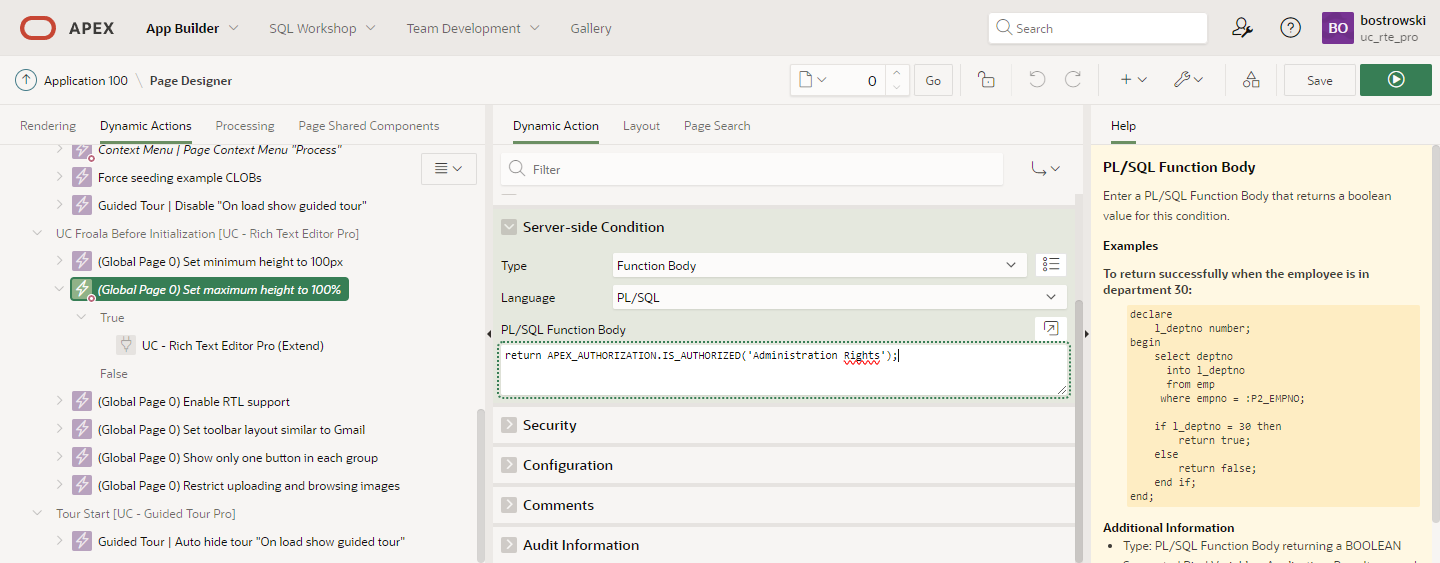
The PL/SQL Function Body code is presented below.
return APEX_AUTHORIZATION.IS_AUTHORIZED('Administration Rights');
Initialization PL/SQL Code
The plug-in page item attribute Initialization PL/SQL Code (application or page item level) allows configuring some of the the plug-in features, supporting process plug-in, and enable or disable third-party integrations. Customizations are exposed through the plug-in package variables and PL/SQL API.
The Oracle APEX function APEX_AUTHORIZATION.IS_AUTHORIZED can be used by a developer to configure user role-dependent configuration, for example enable third party integrations for specific user groups.
See example PL/SQL code enabling third-party integration Wiris MathType only for specific authorization scheme.